Monero, the 10th-largest cryptocurrency by market cap, has carved out a niche by being tightly focused on privacy and security. Where transactions and wallet balances on the bitcoin blockchain are public and transparent, Monero transactions purposefully obscure the amount transferred as well as the sender and receiver’s addresses, building in a high degree of privacy by default.
As an unfortunate but more-or-less inevitable downside, Monero has become the obvious choice of cryptocurrency for anyone wanting to conduct criminal activities without being traced. This is exacerbated by the fact that Monero’s proof-of-work algorithm is designed to make mining viable with a standard CPU, as opposed to the super-specialized ASIC chips which dominate bitcoin mining—so it’s possible for criminals to make money by hijacking victims’ personal machines to mine with.
In response, members of the Monero community have come together to form the Malware Response Workgroup (MRW), as announced yesterday on the Monero blog. Per the description, the workgroup is a self-organized volunteer team focused on providing online information and technical support to users who have the misfortune to be struck by different forms of Monero malware.
The MRW website aims to guide non-technical users through resolutions to three problems: unwanted in-browser mining, unwanted system mining, and ransomware. Currently the information available gives a fairly basic overview of the problems and possible solutions, but visitors are also directed to the #monero-mrw Freenode channel, where they can live chat with members of the group.
The MRW is coordinated by Justin “SamsungGalaxyPlayer” Ehrenhofer and Diego “rehrar” Salazar, two members of the Monero community who took on an organizing role after the idea was proposed in a community meeting in December 2017.
“We started this initiative in the Monero community to show that the wide community of contributors and developers are not in any way supportive of malware and to provide helpful resources for people,” Ehrenhofer explained in an email to BREAKER. “The initiative was recommended by [Monero lead maintainer] Riccardo “fluffypony” Spagni as a way of managing some of the recent reports of Monero being used for malicious mining. While we could not prevent malicious mining, we wanted to start by helping those whose machines had been compromised.”
Ehrenhofer is up front about the scale of the problem, referencing research by cybersecurity firm Palo Alto Networks which concluded that Monero is overwhelmingly used as the cryptocurrency of choice by malicious mining software, and that as much as 5% of all Monero in circulation as of June 2018 may have been mined in such a way. He also points out that the privacy protection and ASIC-resistance of Monero are a distinguishing factor here—and in fact, the same argument could be extended to say that the use of Monero in this context is an endorsement of the efficacy of both measures.
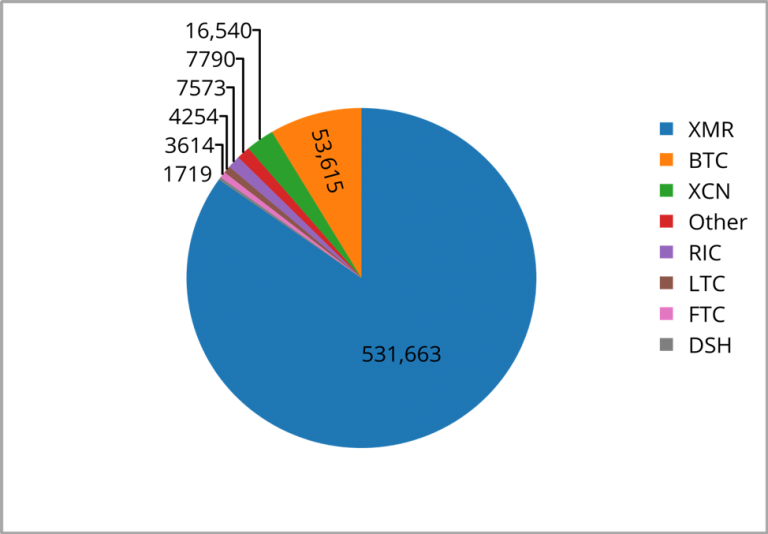
The number of individual malware programs using Monero, as analyzed by Palo Alto Networks.
The MRW is unlikely to prevent Monero from being used for non-consensual mining or ransomware, but it’s a start. Privacy will always be a double-edged sword: technology that enhances it also makes it easier to get away with malicious acts. The Monero community is aware of this, but is strongly committed to the positive values of privacy, too. With better education about risk for non-technical users, and some good old fashioned I.T. support, hopefully the balance of outcomes can stay weighted in favor of good.