The room itself is pretty nondescript—it’s a series of desks lined on the wall, along with another one in the middle. Atop the tables are expensive machinery—motherboards, a few computer monitors—one with a Sega sticker, wires, sensors, gizmos attached to telescope lenses, laptops. A small group of computer whizzes in sweaters hunch over their respective stations tinkering with whatever device they’re trying to digitally blow up. I’m in an attack lab—a part of Ledger’s Paris office that the company usually doesn’t discuss; in fact, I’m the first journalist to ever step foot in here.
Ledger, which builds cold storage hardware, has a team of about eight people whose entire imperative is to hack into its own products as well as its competitors’. The lab, called “Donjon,” has proven successful a few times. Recently, Ledger identified three serious issues with Trezor’s popular hardware wallet, which it passed on to its manufacturer, Czech Republic-based SatoshiLabs (more on this in a minute).
The Donjon—an apt name, given donjon means the inner tower in a medieval castle—looks like, well, a lab. It’s a room with a perimeter of desks holding fancy and expensive machines that produce gibberish-like streams of letters and numbers on all the computer screens. Ledger’s office as a whole is a cavernous series of rooms hidden behind two large and ornate doors in Paris’s second arrondissement. The space itself could be described as a WeWork plopped inside Napoleon’s horse barn. Large rock walls sandwiched around ancient wooden beams surround and envelope the modern workspace. Sleek black metal bars protrude from the old pillars, forming the office’s skeleton. Desks and conference rooms abound—employees lounge on large, cushy office furniture in the open space. Walk downstairs to find yourself in a rock cave that contains an expensive coffee machine, a break-room, and a pinball machine.
A member of the Ledger Donjon team (who did not want to be identified).

Inside the security lair, which resides in a back corner of the office, one security engineer wearing a pullover sweater (the team’s unofficial uniform, it seems) shows me a red circuit board. This device, he says, was built for the Donjon to perform various fault and side-channel attacks. They put a chip on the flat red service, hook it up to a few wires, calibrate it just so, and they begin to simulate how they go about trying to hack into it. (They asked if I wanted to supply my debit card’s chip for the experiment—I politely declined.)
The space itself is meant not just to hack devices, but create a more rigorous security ecosystem throughout the blockchain world. “Our objective is to assess all of the security of everything we do—not only to make sure that we can find all the vulnerabilities in our products [as well as] others’ products,” Eric Larchevêque, Ledger’s cofounder and CEO tells me, “but also to build what we call the ‘targets of evaluation.’” Ledger wants to show what aspects needs to be evaluated in order to prove a product’s overall security. “Once you have these targets of evaluation, you can get evaluated, and this is how you create standards,” he says.
Get the BREAKERMAG newsletter, a weekly roundup of blockchain business and culture.
One fault attack they’ve been attempting focuses on electricity flow. The idea is to trip up a piece of equipment’s firmware by cutting off energy for a split second. When running a set of commands, the Donjon team was able to exploit a glitch on power consumption, which resulted in the firmware skipping an important step. In this case, they were able to bypass PIN entry on a chip used by both the Trezor Key and Keepkey.
Another attack simulation looked at another processor and power consumption. The team used an oscilloscope to track the power consumption as a PIN is entered in a device. In the lab they showed me a function beginning, and then on a screen squiggly lines began to increase, indicating that there was an increased electric signal. And once the function finished, the signal went back down. The Donjon team then looked closer at the signal to see if they could deduce any characteristic traits about what it looks like when an incorrect PIN is entered compared to a correct one. And, it turns out, they could. This sort of side-channel attack illustrated Ledger’s ability to map the electricity and then correctly guess a device’s PIN in an average of five tries. The Trezor device, mind you, allows for 15 PIN attempts until it wipes itself clean.
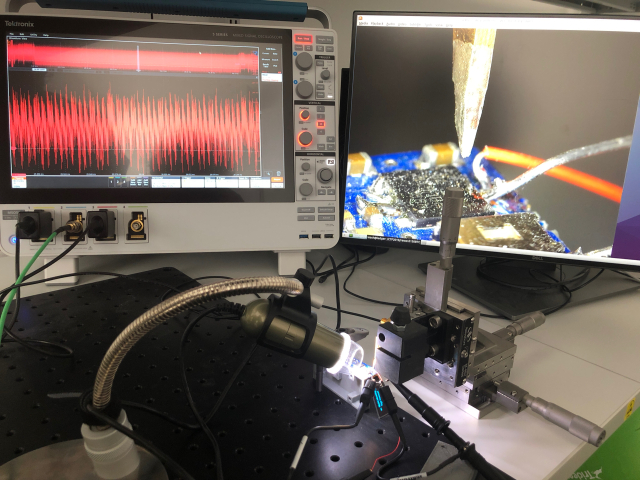
I was a stranger in their lab, someone who only vaguely understood the technical work they do. I walked beside the tables filled with expensive computers and science-grade telescopes and sensors, nodded along with the engineers’ explanations, and tried to glean as much as I could. This team’s work is both tedious and tireless. For example, to calibrate the oscilloscope to detect the electronic signal to even commence the exhibited side-channel attack, they have to calibrate and move the sensors to make sure they are precisely aimed in the right place. If it moves nanometers to the side, the reading won’t be as clear. The engineers tell me it takes days, if not weeks, to find the sweet spot on a chip to direct an attack. And then, when they do, who knows if the attack will be successful. It’s like finding a micrometer-wide needle in a football field-sized haystack.
All three attacks are cautionary tales in the world of crypto-hardware. It’s not enough to put your assets in cold storage and call it a day.
The Donjon has been working for about a year and has already found a few impressive vulnerabilities. They’ve focused a lot of their work on the competition—namely the Trezor One crypto wallet (a popular open-sourced cold storage device that even Jack Dorsey has endorsed)—and found three big ones. One was the side-channel PIN guessing attack I described before (which Trezor just patched in its latest update). The Donjon also proved that it was possible to imitate factory-fresh Trezor devices and pre-seed them with backdoors. Essentially, this meant that someone could buy a Trezor, insert malware into the device that could, for example, send assets to another address, and then gussy it up to make it look as if it had never been opened or tampered with before and resell it.
Of course, this described vulnerability could be extended to most any other device—the world is swimming with counterfeits. The Ledger team, however, wanted to show specifically its ability to reproduce Trezor’s security protocol for its packaging. The team also performed another side-channel attack that would extract the Trezor’s secret key (although, the only way to execute this hack would require knowing the device’s PIN, making it slightly less alarming).

All three attacks are cautionary tales in the world of crypto-hardware. It’s not enough to put your assets in cold storage and call it a day. Larchevêque explains to me that the point of the attack lab isn’t just to find flaws in competitors devices—it’s to make for more accountability in the blockchain industry.
Charles Guillemet, Ledger’s CSO, goes a bit further. Devices like Ledger’s wallet aren’t asked to adhere to many security standards—it’s a buyer beware world out there with few ways to know your privacy is protected. There are a few certification processes these devices are expected to adhere to, but it’s overall left to the companies themselves to build with security in mind. The Donjon, he says, is evaluating both Ledger’s security posture-as well as its competitors—in an attempt to raise the bar. From there, better practices will follow. “I think we need more security certification schemes for this industry,” Guillemet tells me.
Ledger is certainly well placed to take this problem on. A little over a year ago it raised $75 million—which Larchevêque tells me is enough to both grow the company and prepare for for any industry headwinds. Indeed, the company was once profitable during the bitcoin boom and now it no longer is. He reckons Ledger has three solid years of runway, by which time the market should pick back up and propel the business forward once again.
Few people get the chance to see such a space in action—and Ledger’s space is certainly unique given the dual Old French/startup ambiance. In one view you see Rick and Morty paraphernalia, hackers hacking, and ancient rock archways. I imagine other companies will adopt similar security programs, yet I doubt they will have that certain je ne sais quoi.